Voice Assistants Have a Variety of Underlooked Vulnerabilities: Ultrasonic Commands, Cloned Voices, and Even Lasers - CPO Magazine

By A Mystery Man Writer
New type of attack on voice assistants uses ultrasonic waves to access the devices through solid surfaces that are inaudible to humans without the use of special equipment.
News, insights and resources for data protection, privacy and cyber security leaders

ElevenLabs AI Voice Cloning is the Future, by Ivan Campos, Sopmac Labs

SWADE - Interface Zero 3.0 - The Players Guide To 2095

top-5-use-cases-by-surface-01

Spying through Your Voice Assistants: Realistic Voice Command

Hear no evil: Near-ultrasonic attacks on voice assistants

Popular voice assistants like Siri or Alexa easily hacked with

Key Raises Issues of Hacking and Insurance Risks - CPO Magazine

Top 8 Best Voice Cloning Software [2024 New]

PDF) ESSENTIALS OF Business Driven Information Systems
nlp/bayes/description.txt.bak at master · GBWen/nlp · GitHub

Translation, Voice Cloning and Lip Synchronization

Voice Bot Use Cases In Different Industries
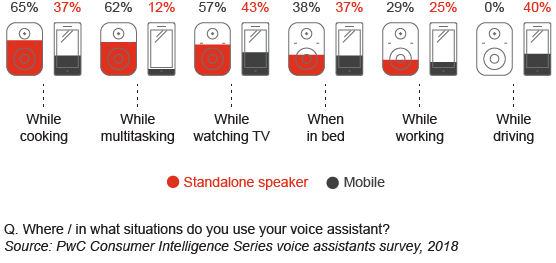
The impact of voice assistants on consumer behavior: PwC

Voice and Local Search: How to Optimize for the Future
- Voice Assistants & Voice Computing – Cyber Security and Avoiding

- Viqal Blog Next-Gen Voice Assistants

- How Voice Assistants Are Transforming Business and Workplace

- Voice Assistants Have a Variety of Underlooked Vulnerabilities

- Compare the Privacy Practices of the Most Popular Smart Speakers with Virtual Assistants

- What are the disadvantages of thick padded bras? - Quora
- Kids & Teens Dance Classes, Camps & Workshops

- Blue Fluted pattern – so Danish, and yet not…

- Bikinis For Women Padded Bikini Top Halter Cheeky Bikini Bottoms Sexy 2 Piece Swimsuit Deep Blue XL

- JBEELATE Women Self Adhesive Bra Lift Up Underwire Invisible Silicone Push-up Bra
